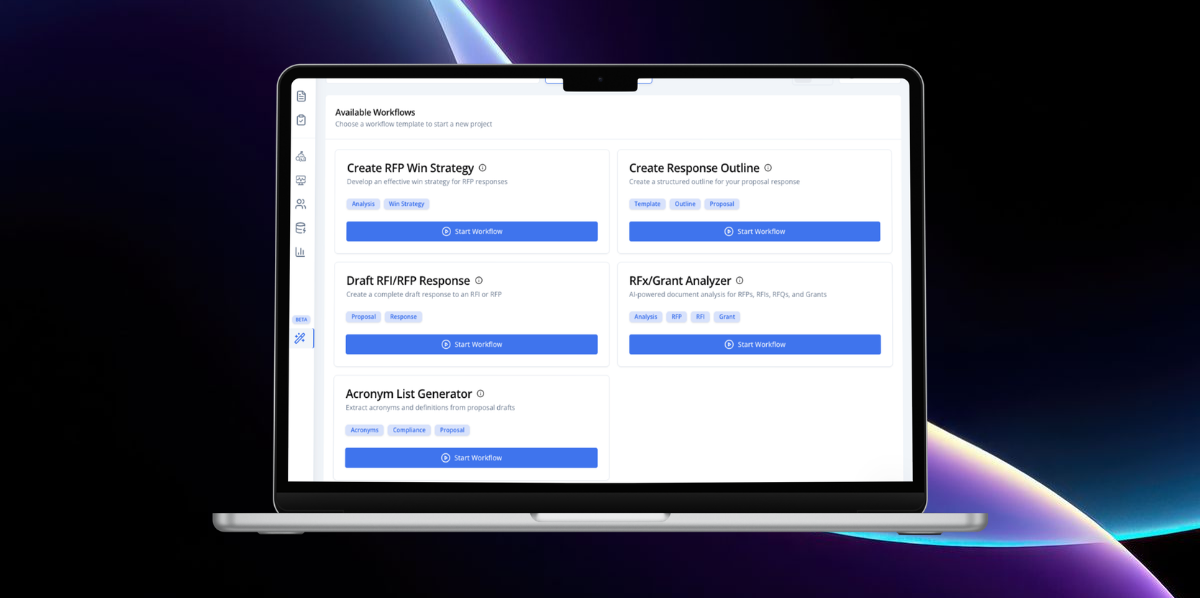
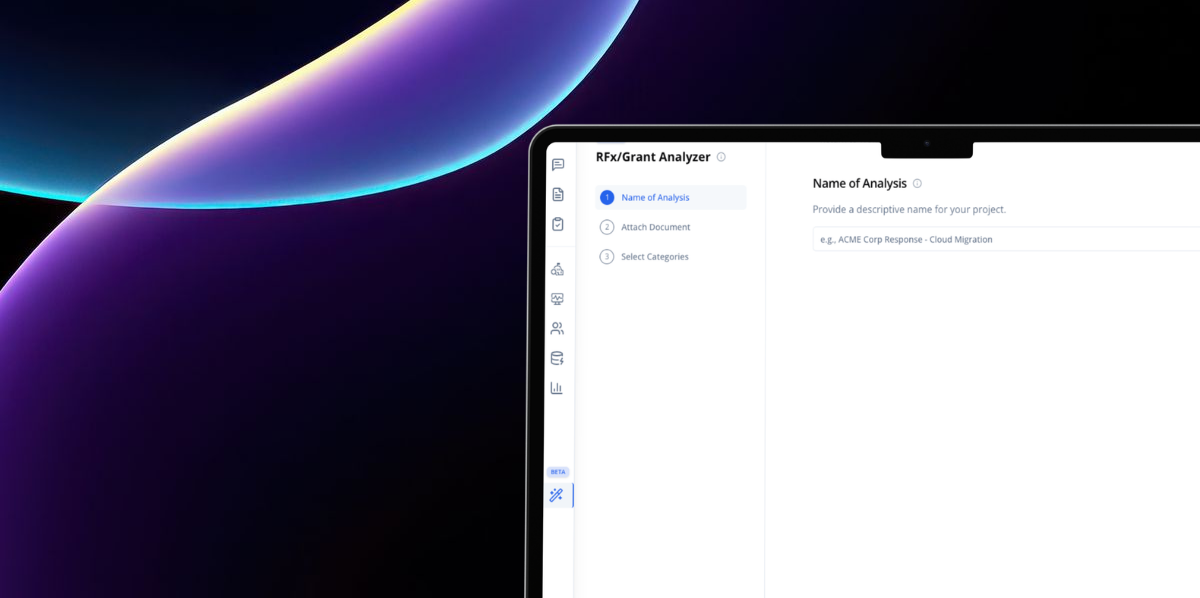
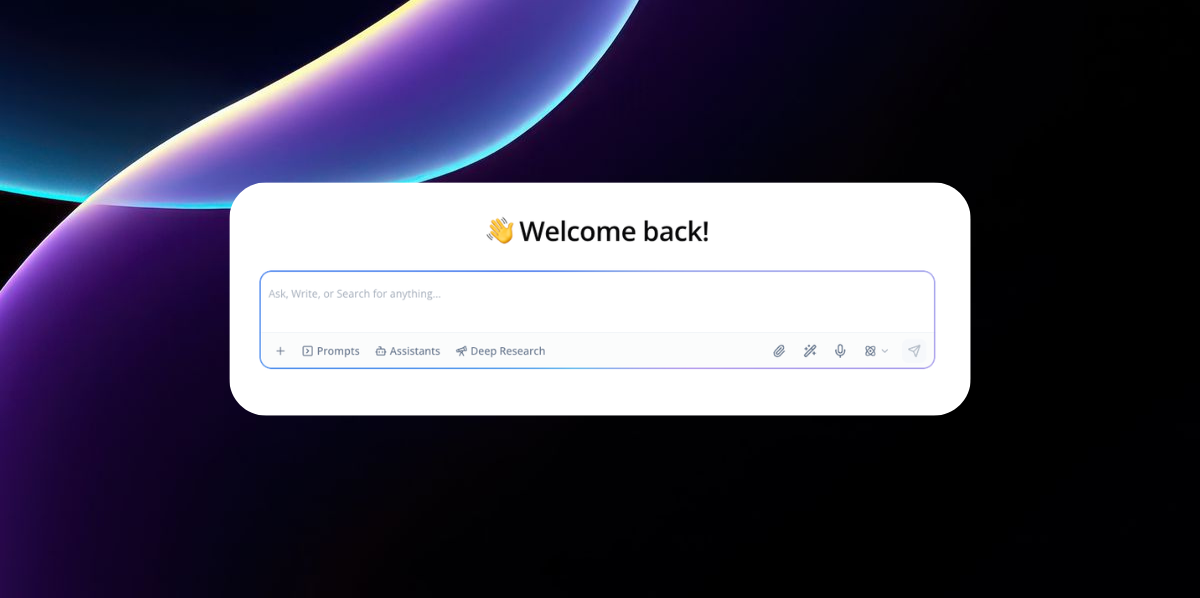
Resource Center
Explore our blogs and e-books to stay up-to-date on the latest news and trends in GenAI, Proposal, Capture and BD AI automation, data and other related topics.
Blogs
Events
Industry Insights

Surviving & Thriving in DOGE: Insights for GovCon Leaders
Surviving & Thriving in DOGE: Insights for GovCon Leaders

NASA SEWP VI: A Deep Dive into its History, Value, and Acquisition Process
NASA SEWP VI: A Deep Dive into its History, Value, and Acquisition Process

GSA Schedules: A Comprehensive Guide for Government Contractors
GSA Schedules: A Comprehensive Guide for Government Contractors
Case Studies

Case Study: How Cutting Edge Communications Achieved 90% Time Savings with Procurement Sciences
Read this Procurement Sciences customer case study to see the real results: 90% time savings on RFP shredding, compliance matrices in seconds instead of hours, and daily use across all proposal operations.
Case Study: How Cutting Edge Communications Achieved 90% Time Savings with Procurement Sciences
.png)
Case Study: How a Mid-Sized GovCon Secured Two Big Wins with Awarded AI
Read the article to find out how a mid-sized GovCon used Awarded AI to streamline proposals, evaluate resumes, and secure two major contracts under tight deadlines.
Case Study: How a Mid-Sized GovCon Secured Two Big Wins with Awarded AI
E-Books

[Free Guide] Introduction to Generative AI: The Future of Government Procurement
[Free Guide] Introduction to Generative AI: The Future of Government Procurement

[Free Guide] AI Prompting Tips: A Comprehensive Guide for Proposal Professionals
[Free Guide] AI Prompting Tips: A Comprehensive Guide for Proposal Professionals

[Free Guide] AI Buyers Guide for Government Contractors: Evaluating SaaS Vendors
[Free Guide] AI Buyers Guide for Government Contractors: Evaluating SaaS Vendors
Webinars

GovCon Made Easy: How Commercial Firms Can Break Into the Federal Market
GovCon Made Easy: How Commercial Firms Can Break Into the Federal Market

SEWP VI Strategies for a Standout Proposal Submission
SEWP VI Strategies for a Standout Proposal Submission

Awarded AI Deminar by Procurement Sciences & Lohfeld Consulting
Awarded AI Deminar by Procurement Sciences & Lohfeld Consulting